Subject to no further problems

I will remove my tools now and give some recommendations, but, I would like you to run for 24 hours or so and come back if you have any problems
Now the best part of the day ----- Your log now appears clean :thumbsup:
A good workman always cleans up after himself so..The following will implement some cleanup procedures as well as reset System Restore points:
Run AdwCleaner and press uninstall
Run OTL
- Under the Custom Scans/Fixes box at the bottom, paste in the following
:Commands
[resethosts]
[emptytemp]
[Reboot]
- Then click the Run Fix button at the top
- Let the program run unhindered, reboot the PC when it is done
Remove ComboFix- Hold down the Windows key + R on your keyboard. This will display the Run dialogue box
- In the Run box, type in ComboFix /Uninstall
(Notice the space between the "x" and "/")
then click OK
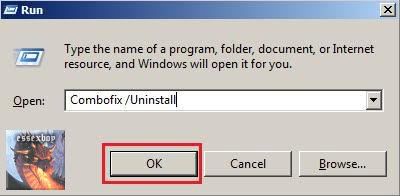
- Follow the prompts on the screen
- A message should appear confirming that ComboFix was uninstalled
Run OTL and hit the cleanup button. It will remove all the programmes we have used plus itself.
We will now confirm that your hidden files are set to that, as some of the tools I use will change that
- Click Start.
- Open My Computer.
- Select the Tools menu and click Folder Options.
- Select the View Tab.
- Under the Hidden files and folders heading select Do not show hidden files and folders.
- Click Yes to confirm.
- Click OK.
Now that you are clean, to help protect your computer in the future I recommend that you get the following free programmes:
 Malwarebytes
Malwarebytes.
Update and run weekly to keep your system clean
Download and install
FileHippo update checker and run it monthly it will show you which programmes on your system need updating and give a download link
If you use on-line banking then as an added layer of protection install
Trusteer Rapport It is critical to have both a firewall and anti virus to protect your system and to keep them
updated. To keep your operating system up to date visit
To learn more about how to protect yourself while on the internet read our little guide
How did I get infected in the first place ?Keep safe :wave: